- Published on
Building and Tracking Secure Software
- Authors

- Name
- Parminder Singh
Secure software refers to applications designed and developed with stringent security measures to protect against unauthorized access and vulnerabilities. It is foundational for maintaining customer trust, ensuring operational continuity, and mitigating financial and reputational risks. We need to look at this challenge as both top-down and bottom-up. In this blog we will explore the key aspects of building secure software, including metrics for tracking security, and the use of frameworks to enhance security.
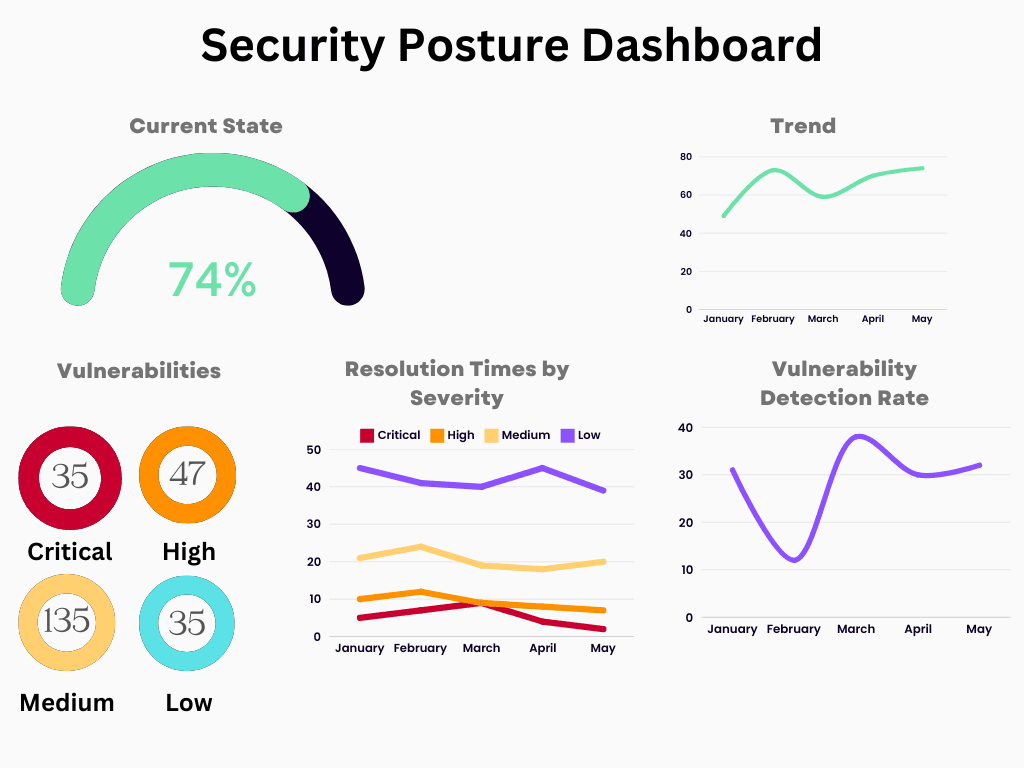
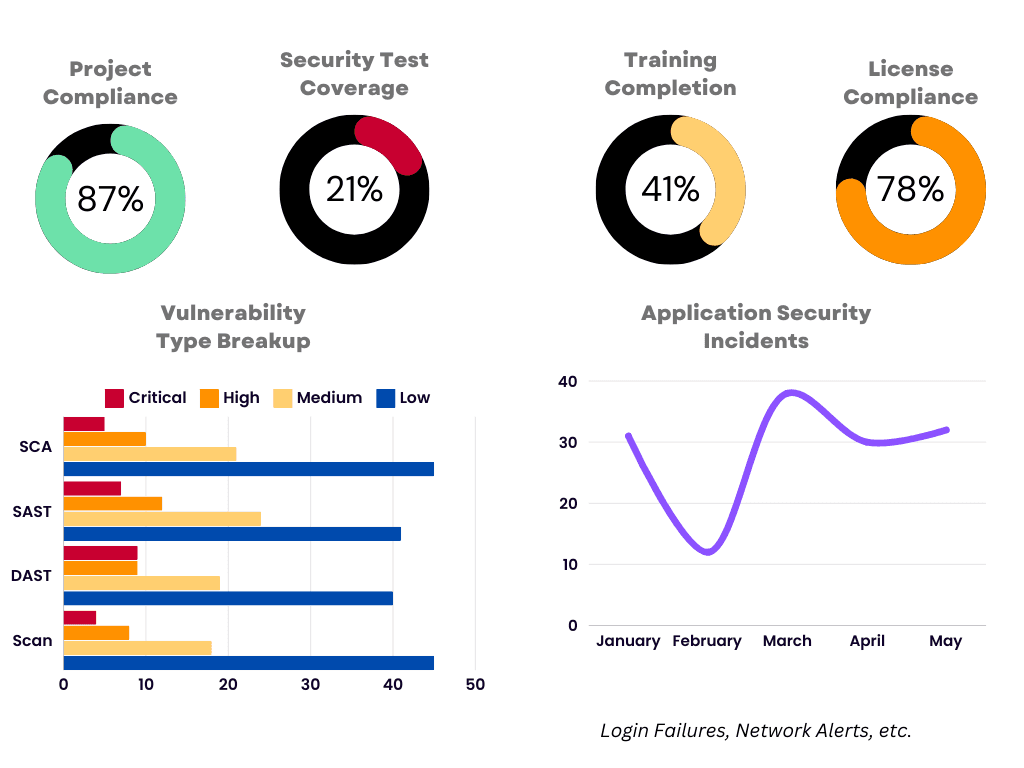
Key Metrics
Metrics are critical for measuring the effectiveness of security practices. Consider tracking the following metrics to assess the security posture of your software:
Vulnerability Metrics:
- Open Vulnerabilities: Total number of open vulnerabilities in the software, categorized by severity (critical, high, medium, low).
- Vulnerability Discovery Rate: How quickly new vulnerabilities are being discovered in the software.
- Time to Remediate: Average time taken to address and close vulnerabilities once they are identified.
Code Analysis:
- Static Application Security Testing (SAST) Results: Metrics from code scans that identify security flaws in software without executing the code.
- Dynamic Application Security Testing (DAST) Results: Metrics from tests that involve executing code to identify runtime security vulnerabilities.
- Software Composition Analysis (SCA): Data on third-party and open-source components used in the software, including known vulnerabilities and licensing issues. SBOM (Software Bill of Materials) is a key component here.
- Container Security Scans: Metrics from scans that identify vulnerabilities in container images used in the software.
Compliance and Risk Management:
- Compliance Status: Overview of compliance with relevant security standards and regulations (GDPR, etc.).
- Risk Assessment Results: High-risk areas in applications, based on the latest assessments. Examples include OWASP Top 10 vulnerabilities, CWE/SANS Top 25 Most Dangerous Software Errors, and MITRE ATT&CK techniques.
Incident Response:
- Security Incidents: Number of security incidents or breaches, including details on their status (resolved, ongoing).
- Incident Response Time: Average time taken to respond to and mitigate security incidents.
Security Training and Awareness:
- Training Completion Rates: Percentage of developers and relevant staff who have completed mandatory security training.
- Phishing Simulation Results: Metrics on how employees respond to simulated phishing attacks, helping gauge awareness and readiness. There's an overlap here with IT security training.
Patch Management:
- Patch Status: Overview of patch deployment across the software, showing percentages of systems patched versus unpatched.
- Critical Patch Deployment Time: Time taken to deploy patches for critical vulnerabilities.
Authentication and Access Controls:
- Failed Login Attempts: Tracking failed authentication attempts that could indicate attempted security breaches.
- Privileged Account Usage: Monitoring the use of accounts with elevated privileges, which are often targets for attackers.
DevSecOps Integration:
- Security Tools Integration: Degree of integration of security tools within the CI/CD pipeline.
- Automated Security Testing Coverage: Extent of automated security tests during the development phases.
Performance Against Benchmarks and trending:
- Security Posture Over Time: Trends in the security posture over time, comparing current metrics to historical data.
- Industry Benchmarks: Comparison of the company's security metrics against industry averages or standards.
A dashboard that combines these metrics can provide a comprehensive view of the software's security posture, enabling stakeholders make informed decisions and prioritize security efforts effectively. DevSecOps can help in tracking these metrics effectively.
Consider adding the following to your DevOps pipelines:
- Dependency and Code Scanning:
- Software Composition Analysis (SCA) Scans: Identify vulnerabilities in third-party libraries and components. If your project uses dependency management tools like npm, Gradle, Maven, Python pip, etc., you can integrate SCA scans into your pipeline. If not, consider using tools like Snyk, Mend.io, etc.
- Static Application Security Testing (SAST): Identify security vulnerabilities in the codebase. Linters and static analysis tools like ESLint, etc. can help identify common security issues in the code by analyzing the source code. These can be integrated into the CI/CD pipeline. These tools can also be integrated within IDEs to provide real-time feedback to developers. This repository lists static analysis tools for all programming languages, build tools, config files and more.
- Dynamic Application Security Testing (DAST): Test running applications for security vulnerabilities using tools like OWASP ZAP, Burp Suite, can be used to perform DAST scans.
- Container Security Scanning: When using containers, leverage tools like Clair, Trivy, and Anchore can be used to scan container images for known vulnerabilities. If you're using Kubernetes, you can also consider using admission controllers to enforce security policies on container deployments. These controllers can be used to block deployments that violate security policies. Tools like OPA Gatekeeper can help enforce these policies. If you deliver software as media files, consider using malware scanners.
- Infrastructure as Code (IaC) Security: Analyze security configurations in IaC templates. This is an excellent guide for security best practices for IaC.
- Security Gates: Implement security gates that prevent insecure code from progressing through the pipeline. If a security test fails, the pipeline should stop until the issue is resolved.
Secure Design principles
Secure design principles are foundational to building secure software.
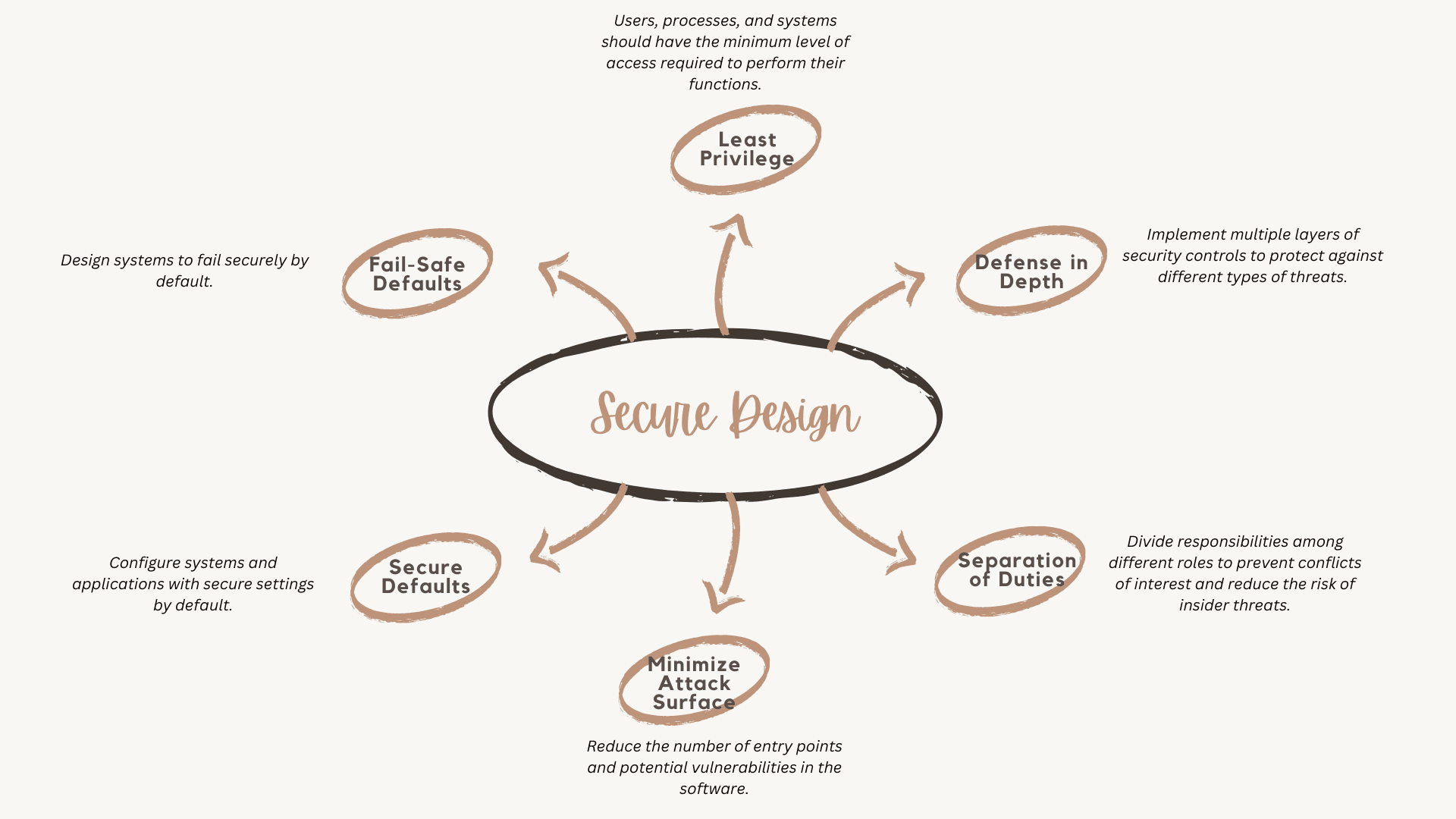
Some key principles include:
Least Privilege: Users, processes, and systems should have the minimum level of access required to perform their functions. This principle helps reduce the attack surface and limit the impact of security breaches.
Defense in Depth: Implement multiple layers of security controls to protect against different types of threats. This approach ensures that if one layer is breached, other layers can still provide protection.
Separation of Duties: Divide responsibilities among different roles to prevent conflicts of interest and reduce the risk of insider threats. This principle helps ensure that no single individual has complete control over critical functions.
Minimize Attack Surface: Reduce the number of entry points and potential vulnerabilities in the software. This principle involves removing unnecessary features, services, and components that could be exploited by attackers.
Secure Defaults: Configure systems and applications with secure settings by default. This principle helps prevent misconfigurations and reduces the risk of security incidents.
Fail-Safe Defaults: Design systems to fail securely by default. This principle ensures that in the event of a security breach or failure, systems revert to a secure state or shut down to prevent further damage.
Here's a good read on Secure Design Principles.
Security Frameworks
Consider applying the following security frameworks to enhance the security of your software. These frameworks provide guidelines, best practices, and controls to help organizations build secure applications:
ISO/IEC 27001: This international standard outlines requirements for an information security management system (ISMS) to protect sensitive information.
OWASP Application Security Verification Standard (ASVS): This standard provides a checklist of security requirements for designing, developing, and testing secure applications.
CIS Controls: Developed by the Center for Internet Security, these controls provide a prioritized set of actions to protect organizations against common cyber threats.
Conclusion
Building secure software requires a holistic approach that encompasses metrics, DevSecOps practices, security architecture and engineering, and the use of security frameworks. By integrating security into every phase of the software development lifecycle, organizations can reduce security risks, protect sensitive data, and build trust with their customers. Investing in security early in the development process can save time and resources in the long run, ensuring that software is resilient to cyber threats and meets compliance requirements.